One of the biggest problems that I saw with DNP and WSP still seems to persist in this version; that is the fact that the server site runs as an administrative user. This allows a compromised site running ASP or .net to be able to extract the credentials for this account from the MetaBase.
To make matters worse, if the server si on a domain then they can use tools like Mimikatz to capture domain level credentials and spread filth across your entire windows domain. I would really like to see the sites use non-admin credentials and then talk to a backend service that has the admin access. This would greatly reduce the risk associated with using this product.
Additionally, this product should handle filesystem permissions like Plesk does; that is lockdown filesystem access for the SCP_IUSRS group so that the group has no access to anything they do not need, and there should be a system in place where you can tell SCP what custom permissions it should set for this group on third party objects that SCP doesn't just know about.
The lack of these two things is preventing us from deploying this product.
Hello,
Running it as administrator user can be done in 2 ways (atleast for domain based systems)
- You can assign it administrator member groups in the application pool (i'm assuming this is what you do not want)
- You can fill in administrator account in the Active Directory Settings section when you set it to "secure"
However it does need higher system level access in order to create the resources for you. so one way or another the SolidCP Server module requires administrator level access.
It also only needs this for the SolidCP Server module, no other website needs (or gets) this kind of access. so when a site is breached they should never be able to climb up the ladder and find out your administrator access (assuming the server is hardened properly).
To your second point:
WebsitePanel more or less assumed that the system administrator locks down their own system (so removing users group from c, adding deny rights to system32 folders, etc)
however Marc has been working hard on automating the deployment, configuration, and hardening for you with his configuration script available here:
http://installer.solidcp.com/Files/1.0.4/Tools/SolidCP-Configuration-Tool-1.0.4.zip
This will automate most of the hardening aspects at this point (it does not yet do SSL optimization though).
Regards,
Marco
Hello Marco,
My point is that a website should never run with admin credentials, especially not domain admin. On a shared hosting server there is always a way for an attacker to gain access to information in the metabase. In fact, prove it to yourself, set up a server with SCP, lock it down as you say you should, put a site on it, put a copy of aspxspy on one of the sites, then have fun reading registry information and metabase properties. If you haven't seen this happen then you either don't run production shared hosting servers, have been very lucky, or just aren't checking out what is happening on your servers. This isn't the only tool out there, one the worst is mimikatz, it doesn't even have to be downloaded, it can just be loaded into memory and executed.
Well to keep it simple:
SolidCP Server (and anything that needs to create system resources) needs to have administrative access one way or another, SolidCP, Plesk, and other panels are not an exception to this. without one form of administrative access (if it's login codes so login as admin then execute by powershell, if it's the app pool it self to allow you to access the system resources, etc.. that ofcourse is entirely up to the program where SolidCP supports both).
In the very end, a user with no access to the C disk --> Can't make a folder on the C disk, or apply permissions for the new site user, create a new Site user, or create an IIS Website on the system. this is just OS basics that everyone has to comply to.
I have multiple live web servers, with 4000+ sites (all actively used) and running for over 5 + years, servers are heavily monitored and well looked after, we have not had any system level intrusion, sites like Wordpress / joomla / dnp ofcourse do get hacked, but with our setup that can't walk further then their own site. (which if spreads malicious content will be suspended etc.)
I do wonder if there's some confusion about which sites you think have administrative access?
As for SolidCP it's only the SolidCP Server (which you usually lock down to specific ip's only).
any other website it creates (customer websites) have minimal access just to their own directory, with their own site user etc.
I tried to load your example. after allowing it in our exceptions list (as by default my system removes it instantly due to threat) --> the only thing you can actually get with it is system processes. (with limits)
here's some screenshots:
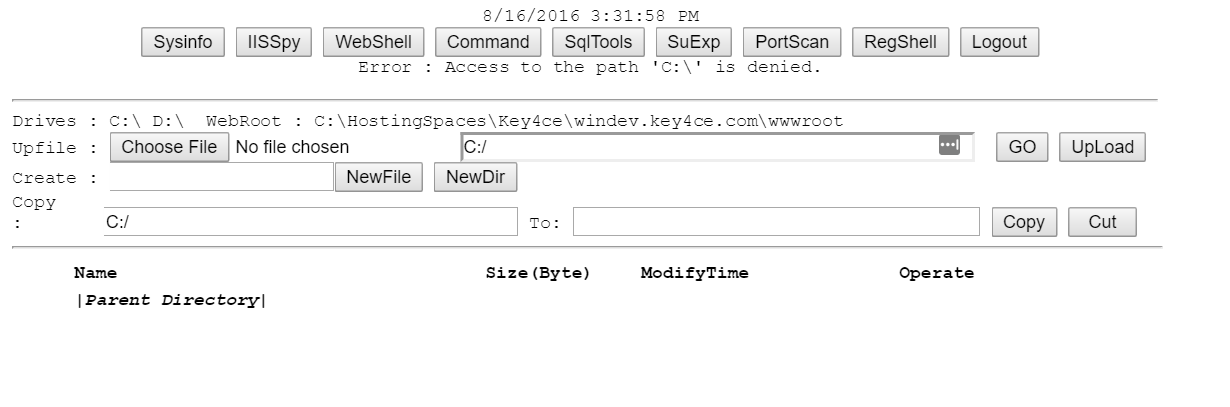
As you can see: Access is denied as any decently configured Windows Web server should give.
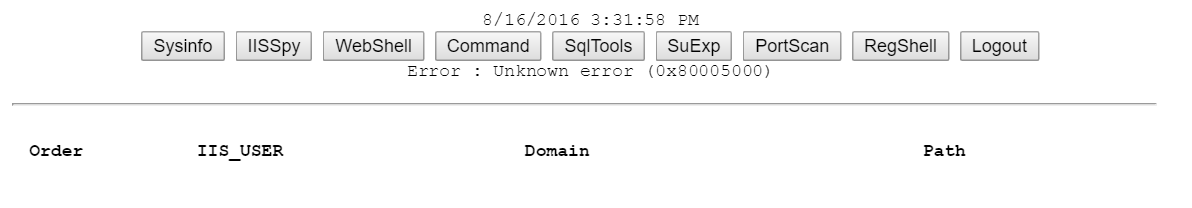
It can't read any IIS site / app pool / user, as a site has no such access to it.
for CMD it's ofcourse denied too:
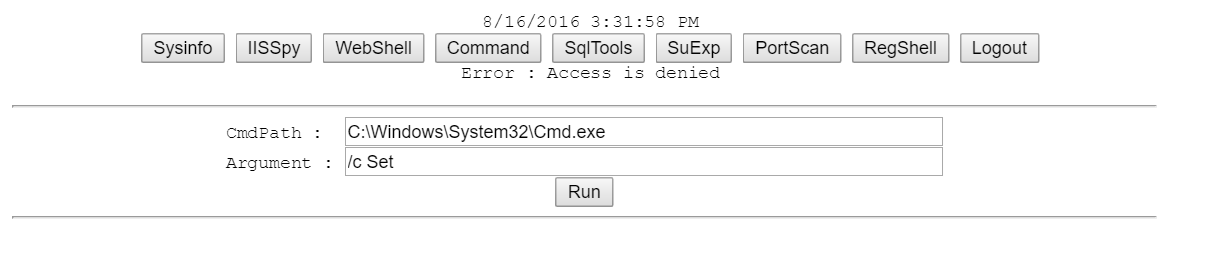
In the end, none of my customer sites have any such rights, The SolidCP Server is locked behind firewalls, and only allowed by specific internal ip's. (so no chance this kind of tool ends up on the SolidCP Server site that can actually preform these actions).
I understand fully that the CP needs admin access, I am just saying that the SITE shouldn't have admin credentials. Also, you should try that IISSpy option on a site that is running with .net full trust. Which unfortunately we have to allow in some of the environments we manage because our clients demand that their clients be able to do so.

